500,000 个 WooCommerce 网站遭到黑客攻击
WooCommerce-payments 插件中存在严重的身份验证绕过问题

在 WooCommerce 支付插件中发现新的安全漏洞
在 YouTube 上观看 Exploit: RASP protects website from authentication bypass
CVE 详情: No CVE has yet been issued (March 28, 2023)
WooCommerce 声明: developer.woocommerce.com critical vulnerability
A newly discovered security vulnerability in the WooCommerce Payment Plugin has been found, which affects versions 4.8.0 to 5.6.1. The vulnerability has a CVSS score of 9.8 marking it as urgently critical. Exploitation of the vulnerability results in complete system compromise with attackers gaining complete control over the affected website.
The vulnerability exists in the “determine_current_user_for_platform_checkout” function, which uses the Wordpress "determine_current_user" filter and takes untrusted user input directly as the user id of the current user, bypassing all authentication requirements. This security bypass flaw can be used to impersonate any user on the website with full permissions.
The security researcher participating Michael Mazzolini in the HackerOne bug bounty program reported the vulnerability directly to the woocommerce team. They have decided to not issue a CVE until April 6, 2023 to allow users time to update their vulnerable software. BitFire has decided to not release the specific details on how to exploit the vulnerability while users are still updating their websites.
However this flaw is simple to exploit and find, and is being currently exploited on the Internet. BitFire has seen a recent upswing in Authentication Bypass RASP firewall denies linked to this attack. It appears that several bot nets are currently targeting WooCommerce websites with exploit code to create backdoor accounts. Site administrators running the WooCommerce Payment Plugin are advised to review all current user accounts on their system, change passwords, and run a complete malware scan on their website.
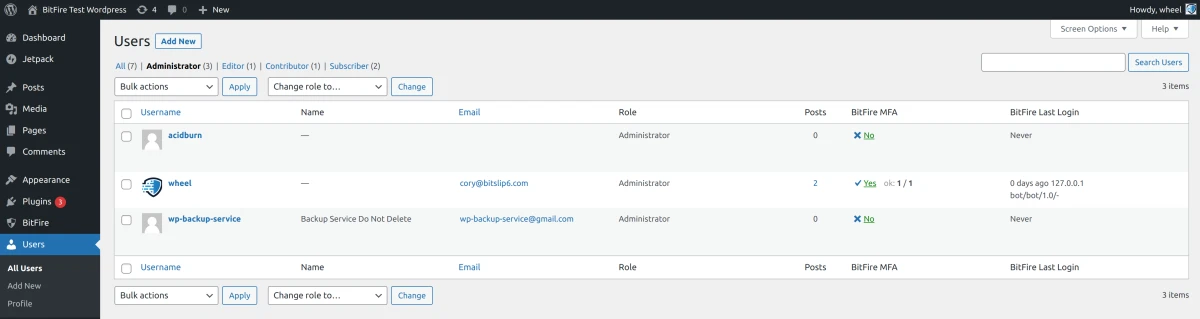
审查用户账户
Observed attacks are attempting to create backdoor administrator accounts on vulnerable web-sites. Administrators are urged to review all current administrator accounts on their websites. If any unknown accounts are found run a comprehensive full malware cleanup procedure.
查看 HTTP 访问日志
We have collected some sample exploitation attempts and administrators can review logs to check for compromise attempts. Sites running the vulnerable plugin can review their HTTP access logs and look for lines similar to the following:
108.171.120.25 - - [26/Mar/2023:18:33:09 -0600] "POST /?rest_route=/wp/v2/users HTTP/1.1" 200 2283 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:111.0) Gecko/20100101 Firefox/111.0"
Note the 200 response code and the 2200 byte response size. Successful exploitation will have a similar response size in the logs. Failed exploitation due to blocking from a RASP firewall will result in a 403 resposne code indicating the attack was stopped.
运行完整的恶意软件扫描
在检查网站是否存在未经授权的管理员账户后,必须检查网站是否存在任何可能上传的恶意软件。
Use a complete malware scanner like the one included with the BitFire security plugin or another high quality malware scanner like MalCure
运行时应用程序自我保护可防止身份验证绕过
It is important to note that traditional Web Application Firewall (WAF) solutions are unable to block this type of attack. Only a Runtime Application Self-Protection Firewall (RASP) like BitFire is capable of stopping authentication bypass attacks.
BitFire RASP prevents this attack out-of-the-box by monitoring the WordPress authentication path and requiring at least one valid authentication method has passed to allow the request. We created this You-Tube video to show exactly how this vulneraiblity is exploited and how a RASP can prevent this type of attack. RASP protects website from vulnerable website from exploit
the newly discovered security vulnerability in the WooCommerce Payment Plugin requires urgent attention from site administrators who are using this plugin. By following the recommended precautions, administrators can help to mitigate the risk of their website being compromised by attackers. Additionally, using a RASP solution like BitFire can help to provide an extra layer of protection against authentication bypass attacks.