BitFire Dashboard
version 4.0.0+
BitFire Dashboard Usage Guide
Understanding the BitFire Dashboard
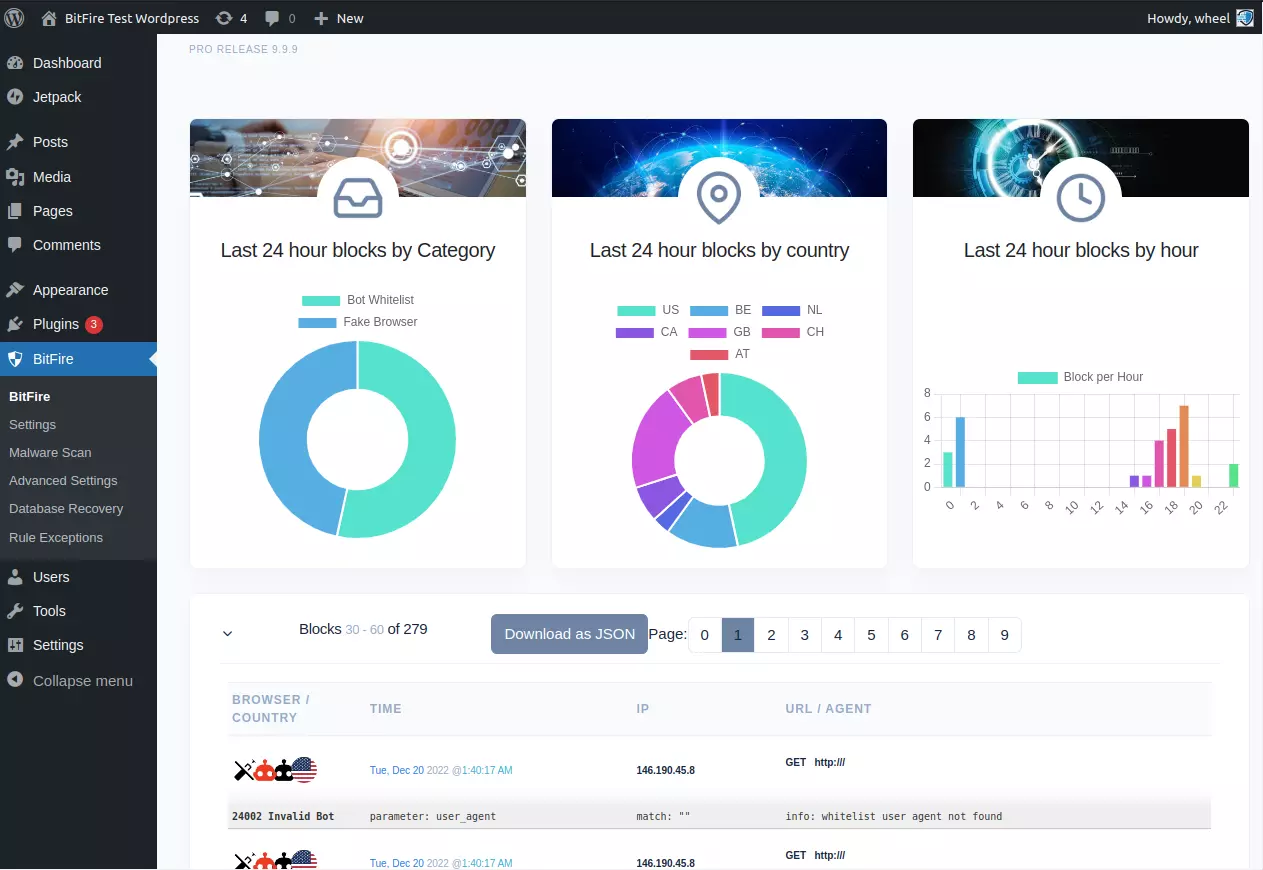
The Dashboard allows you to view the BitFire weblog which includes all blocked traffic and optionally, all passed traffic. The free version of BitFire has a rotating log of 512 entries and paid versions include 32,000 events. You can use the BitFire dashboard to understand the security posture of your website as well as general traffic patterns when "log everything" is enabled in settings.
If you do not see requests that you are expecting to see in the log when "log everything" is enabled the most likely reason is a caching plugin or cache system by your hosting provider served a cached version and BitFire never saw the request.
Click on the red X next to your IP address next to the "Exclude Filters" to see requests from your own IP.
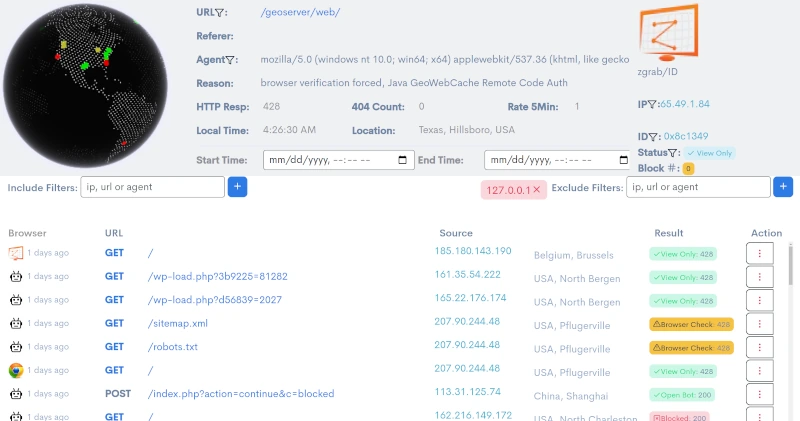
Result Column
The most important section of the dashboard to understand is the "Result" column. This column gives detailed information about how the request was handled. The result includes a color coded text description of how BitFire handled the request and the HTTP response that was served by either WordPress (usually a 200) or BitFire block or JavaScript challenge code (configurable in settings).
OK IP
Network JavaScript Fingerprint No Data No CheckThese status codes indicate that the Web Browser or Bot has been authenticated by either Fingerprinting, JavaScript challenge or IP or Network authentication for bots. Green badges indicate real human web browsers or trusted (or open) bots. Bots can be configured on the Bot Control page.
Browser Check
Browser Checks are served to to anything identified as a browser that did not send a valid Fingerprint. BitFire maintains Fingerprints for about 20 browsers on multiple mobile and desktop platforms.
Most hacking, spamming and scanning tools will be stopped by Browser Checks. This is because most malicious tools identify themselves as web browsers but do not have matching fingerprints. BitFire serves a Browser Check and the tool either stops, or will continue scanning and being served Browser Check pages. You can control how the Browser Check displays in the settings page.
Blocked
Blocked requests are much more rare with "Require Full Browser" option enabled. These are requests that have been blocked by the firewall, or the RASP and indicate a strong likely hood of attack. Occasionally legitimate requests can be blocked by the firewall. If this happens, click on the action and select "Unblock Request".
You can configure the Firewall exceptions, IP and User-Agent pass/block configuration on the BitFire exceptions page.
Action Column
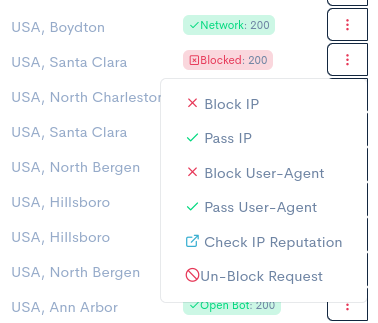 The next section to understand is the "Action" column. The action column controls how to allow or block
any request by it's IP Address, User-Agent, and also unblock any firewall rules and lookup IP reputation data for any request
to your website.
The next section to understand is the "Action" column. The action column controls how to allow or block
any request by it's IP Address, User-Agent, and also unblock any firewall rules and lookup IP reputation data for any request
to your website.
You can use these actions to allow or block any request by it's IP address or user-agent. This can be very helpful for allowing bots that report themselves as a web browser and are then served the browser check page which prevents them from working. Simply allow the requests based on the IP, User-Agent or both.
If you are unsure if a request is legitimate, click on the check IP reputation button to view detailed IP reputation data from abuseipdb.com.
Global Location 3D Globe
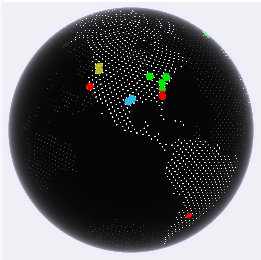 Near the top of the screen you can see the global map with colored pins for each request. The pins are color coded the same
as the Result badges; Browser Check - Orange, Pass - Green, Blocked - Red. The currently selected request will be centered
and highlighted in Blue.
Near the top of the screen you can see the global map with colored pins for each request. The pins are color coded the same
as the Result badges; Browser Check - Orange, Pass - Green, Blocked - Red. The currently selected request will be centered
and highlighted in Blue.
Browser Identification
 Browser's are most commonly identified by their User-Agent header which is sent with every web page request.
Each web browser self-identifies with a unique user-agent that identifies it to the server. As you can guess
the problem with this is anyone can say they are any user-agent.
Browser's are most commonly identified by their User-Agent header which is sent with every web page request.
Each web browser self-identifies with a unique user-agent that identifies it to the server. As you can guess
the problem with this is anyone can say they are any user-agent.
There are 2 types of requests. Requests from human operated web browsers and requests from automated bots and tools, like Google, Bing, SEO-Moz, etc. BitFire maintains info on over 180 unique browsers and tools and over 3,500 commercial bots.
Identifying Real Browsers - Blocking Fake Browsers
Many hacking tools report themselves as old version of Chrome, Firefox or random rotating web browsers from a large list. How can we tell if a request that claims to be Firefox, is really Firefox or a hacking tool? Bit Fire uses 2 methods.
Browser Fingerprinting is the first method. Every web browser has a unique fingerprint in the details about how it sends each request. There are 1,307,674,368,000 possible BitFire browser signatures and only 2 dozen valid signatures for each browser type. Requests with matching fingerprints are flagged as valid and allowed to access the website.
Browsers failing fingerprint challenge are sent a small JavaScript challenge. This challenge will be automatically filled out by the web browser's JavaScript and sent to the server. If the challenge passes a cookie is set and the firewall serves the originally request page and allows further traffic.
Browsers identified with version /ID are requests that matched a fingerprint for some malware type NOT the user-agent sent with the request.
Identifying Real Bots - Blocking Fake Bots
The second type of request is one from an automated tool like Googlebot, bingbot, and other online tools like WordPress's JetPack. These requests can not be verified like the browsers because most do not process JavaScript code. When BitFire identifies a bot, it checks the BitFire bot database of over 3,500 known bots and tools. BitFire then checks the bot's source IP Address and Network to verify if it matches a known bot.
Bot's claiming to be Googlebot coming from Serbia are denied access because they do not match Google's server network. If the bot is unknown to the BitFire database, the source IP address is checked against a real-time updated blacklist IP database. IP's from low reputation are added to the "unknown bot" list and flagged for blocking. If the IP reputation for the unknown bot is good, the request is allowed. This can be configured in the BotControl panel for every unique bot.
Searching Traffic Logs
All include filters are displayed on the left side of the dashboard in green and exclude filters are displayed on the right side of the screen in red. All of these filters may be removed by clicking on the X in the filter badge.
The free version of BitFire maintains a rotating list of the last 512 requests. You can page through the data by using the left and right grey chevrons in the center of the dashboard. PRO versions of BitFire maintain logs for the last 32,000 requests. All of the log data is searchable by IP Address, URL, User-Agent , Result or ID (0x fingerprint). You can type in any portion of an IP address, URL, User-Agent, or an exact result action (view only, no check, blocked, fingerprint, browser check, etc) or exact fingerprint into the include filters on the left, or the exclude filters on the right. Pressing the blue plus button will then either add that filter to the list of traffic to include, or exclude.
Multiple filters may be stacked in both the include and exclude filters and only requests matching ANY of the include filters and ALL of the exclude filters will be displayed. The refresh rate will be slower if filters exclude most requests since the entire log must be searched for each refresh (60 seconds). You can speed up the search process by adding date ranges for the search to limit how much log data must be searched.
The interface also has several filter icons in the top header that allows you to use a single mouse click to filter to just the current attribute.