BitFire Core Einstellungen
Version 4.1.10+
BitFire Ultimativer WordPress Sicherheitsleitfaden
BitFire Core Einstellungen
Auf der BitFire-Einstellungsseite können Sie jede von BitFire angebotene Sicherheitsoption aktivieren und deaktivieren. BitFire FREE enthält die umfassendsten Bot-Blocking-Funktionen für WordPress, die es gibt.
Bot-Blocking ist entscheidend für die Sicherheit Ihrer Website. This free tool instantly stops brute force attacks, credential stuffing attacks, SPAM, wpscan, nmap, nicko, nessus, python exploit scripts and any other hacking tool targeting your website.
TL;DR: Enable all marked options and put an end to web attacks!
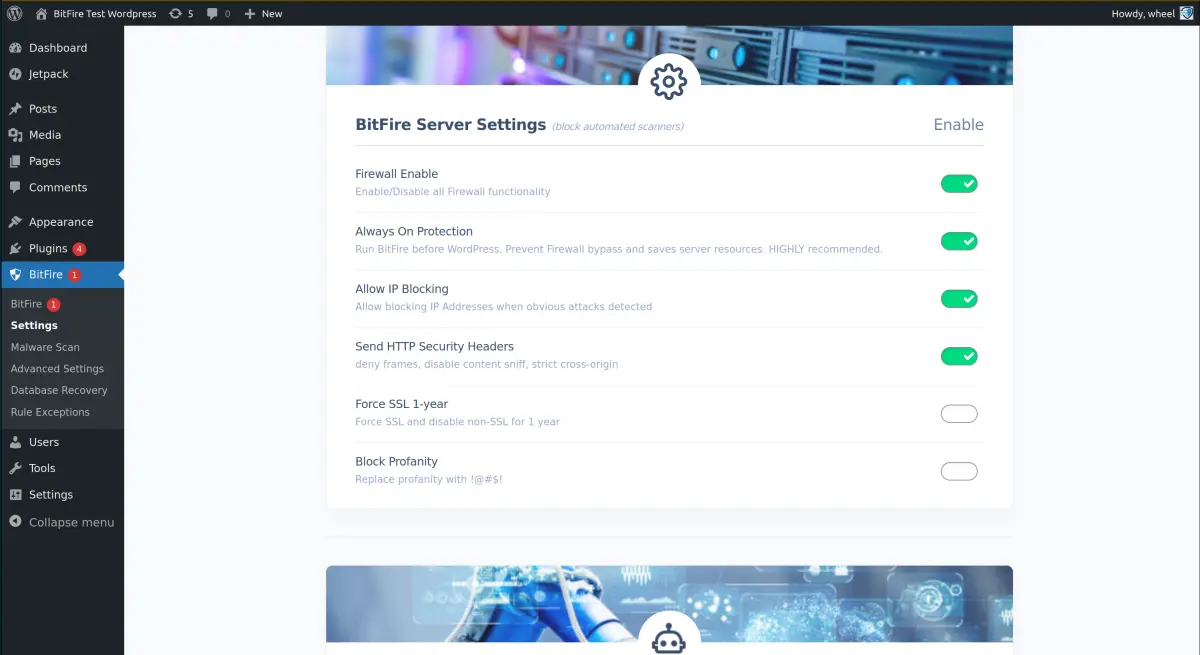
BitFire Server Einstellungen
- "BitFire Enable": Disabling this switch will turn off all Firewall, bot-blocking, logging, header, and RASP features. This is equivalent to disabling / uninstalling the WordPress plugin without disabling it.
- "Always On Protection": Add BitFire to you user.ini auto_prepend startup. This is equivalent to WordFence "Optimize Mode". It can provide additional protection for your website. There is slight risk on some hosting providers do not support this feature well. Please ensure correct firewall functioning before enabling this feature. (5 min update time for PHP to see this change enabled or disabled)
- "Log Everything": BitFire includes a binary access log capable of logging all HTTP requests to your server. By default it will log all browser checks and blocks. Enabling this feature will tell BitFire to log ALL requests, including allowed requests. The FREE binary log size is 512 events. PRO log size is 32,000
- "Disable XMLRPC": Disabling XML RPC can increase the security of your website if you do not use it. Notable examples include JetPack integration, and the official WordPress mobile app. Notable security risks include automated login attacks. (NOTE, this are blocked with correct configuration of Bot Blocking)
BitFire Sicherheits-Header
Im Gegensatz zu dem, was Ihnen viele WordPress-Sicherheits-Plugins erzählen. Es gibt eine kein XSS-Schutz mit HTTP-Headern . Content Security Policies bieten jedoch einen hervorragenden Schutz vor XSS, Redirect-Angriffen und vielen anderen Browser-Angriffen. Die Konfiguration kann für viele Websites frustrierend sein. Unsere PRO-Autokonfigurationsoption wird für schwierige WordPress-Konfigurationen empfohlen..
- "Send HTTP Security Headers": Send the core HTTP security headers. These options instruct the web browser how to handle data in a more secure way. And are compatible with 99% of websites.
- "Require SSL": Send and HSTS header instructing browsers to never connect to your site without using SSL. This feature is recommended for most sites, however if your SSL certificate expires, your website will not be accessible in any way until the certificate is updated.
- "Send Content Security Policy": Send a global content-security policy to web browsers not accessing your front end web content. This requires adding every domain that your sites loads resources from to the included text area. After enabling this option load your site, find what breaks and add those domains to the editable list. If possible, remove any 'unsafe-inline' resources.
- "Send Permission Policy": The permission policy controls which APIs are available on your website. This can be used to restrict access to the browser camera, microphone, geo location services, etc. Restricting this access will prevent any possibly malicious JavaScript from accessing those client mobile resources. The default option disables most additional features.
- "Deny Cross Origin Resource Sharing": This option controls how your web site will handle external web sites making dynamic requests to this site. Enabling this feature explicitly denies these potentially dangerous client side requests. Compatible with >99% of sites.
BitFire Bot-Blockierung
Bot Blocking ist die wichtigste Funktion, die Sie für Ihre Website richtig konfigurieren müssen. Die korrekte Unterscheidung zwischen echten und gefälschten Browsern und zwischen guten und schlechten Bots macht Brute-Force-Angriffe, das Ausfüllen von Anmeldeinformationen und das Scannen von Schwachstellen unmöglich und verhindert sogar, dass sich Exploits jemals mit WordPress verbinden.. Es funktioniert in 2 Schritten: Browser oder Bot identifizieren, dann blockieren, was nicht.
Schritt 1, Identifizierung von Browsern. BitFire verfügt über Identifizierungsinformationen für über 100 verschiedene Browser und kann mit einer einzigen Anfrage sofort Fingerabdrücke von 95% der Brauer erstellen.. Es ist wichtig zu verstehen, dass jedes Spam-, Hacker- oder Exploit-Tool, das den neuesten Chrome-Benutzer-Agenten verwendet, NICHT dem korrekten Fingerabdruck für Chrome entspricht.. 100% dieser Hacking-Tools werden nicht in der Lage sein, auf Ihre Website zuzugreifen und werden immer nur eine "Browser Verification JavaScript Challenge" erhalten, ähnlich wie Cloudflair. Echte Browser kommen durch, 100% der Bots werden gestoppt.
Schritt 2: Bots identifizieren. Es gibt 2 Arten von Bots, gute Bots wie googlebot, und schlechte Bots wie nmap oder zgrab. BitFire unterhält eine Liste von über 3.000 bekannten guten Bots mit passenden IP- und DNS-Authentifizierungsinformationen. Good bots are authenticated and allowed, "Unknown Bots" have reputation data checked and a decision made based on IP reputation.
Vergewissern Sie sich, dass Sie Ihr Bot-Kontrollpanel überprüfen, nachdem Sie BitFire ein paar Tage lang betrieben haben.
- "Require Full Browser": This option will verify browsers are real humans by fingerprint or send a JavaScript challenge page. This option stops 99% of bot attacks which will show up in the dashboard as "Browser Check"
- "Allow Only Approved Bots": This option will verify that anything not identified as a browser, will be verified against the site bot list configuration. By default only verified good bots and high IP reputation IP addresses are allowed. Be sure to review the Bot Control configuration to make sure you haven't blocked any plugin access.
- "Block Hacking Tools": This option instantly block any bot connecting to your website with a User-Agent of a malicious tool like wpscan, nmap, etc.
- "Block Plugin & Theme Scans": This option will confuse plugin and theme scanners by detecting these scans and replying with random data for each plugin scanned. This will confuse any scanner and return bogus data for all scans.
- "Do Not Bot Check Ajax Requests": This option is only necessary for sites with page caching enabled and dynamic ajax requests on the user facing website. Page caching intercepts the normal browser verification step, sending an XMLHTTPRequest as the first seen request. For some sites also running behind a proxy, this can fool fingerprinting into thinking all requests are invalid. Enable this option if you have problems with AJAX requests for users.
- "Block Web Scrapers": By default, BitFire will allow any browser, or bot to access your site to view any page. Enabling this option requires all browsers and bots to verify before accessing any page, even if just for viewing
- "High Sensitivity Block Mode": This mode is restricted to users with Premium support. It changes the default block mode from reputation check (128 free reputation checks) / open, to always closed for unknown bots.
- "Challenge Style": Select which JavaScript challenge to display for browsers with unknown fingerprints. You can select a simple white page, spinner, BitFire verification screen, or emulate the cloudflair light and dark themes pages.