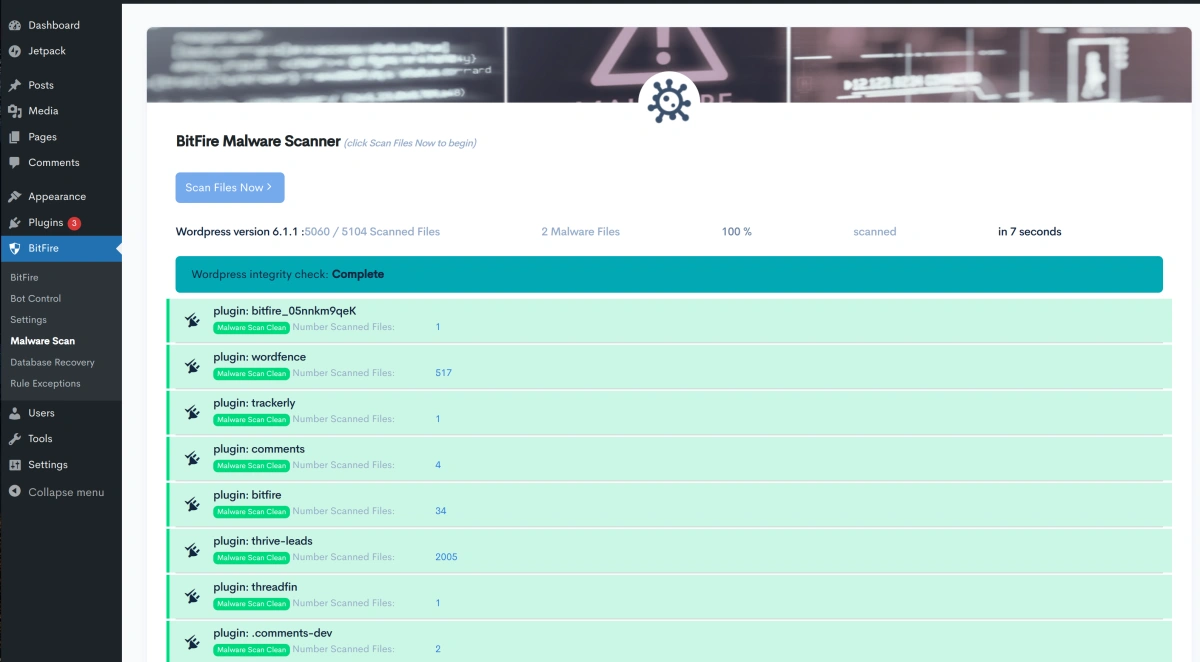
BitFire Malware Scanner
version 3.5.1+
BitFire Malware Scanner Guide
BitFire Malware Scanner
The BitFire malware scanner has detailed signature data for over 10,000,000 WordPress core, themes and plugin files in the BitFire remote API. Leveraging this deep technical data about WordPress PHP and JavaScript files, BitFire is able to scan for malware at a rate of over 10,000 files per minute on most hosting providers.
The malware scanner searches first for all files that it has signature data for. The local file signature is then compared to the known signatures and all matches are validated. The remaining files are then reduced to just differences with the original file and unknown files are treated as entirely unique. These differences are further reduced to any with the ability to execute remote code or upload new files.
Once we have the final list of of unknown code that can potentially run harmful functions, we further examine the code examining programming style white-space, functions used, character frequency analysis and other metrics to determine if the code is malware or benign WordPress code. On average BitFire identifies a false positive malware file at a rate of about 1 in 2,500.
Since most WordPress installs have about 10,000 files, on average you can expect BitFire to identify about 4 malware files on your install that are actually benign and take about 60 seconds to do so. After the initial scan, additional BitFire malware scans should complete even faster.
Identifying Malware from Software
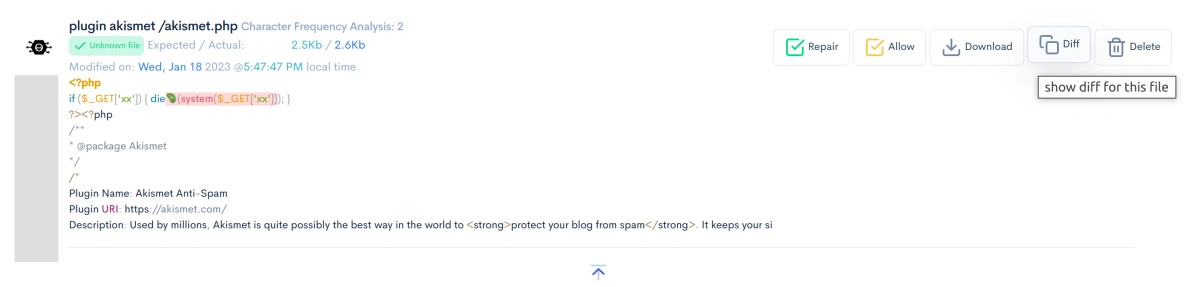
It is worth the time to investigate each identified malware file and make a manual determination if it is clean or not. To do this, click on the "diff" button next to the file. All files differences are shown and identified potentially malicious program lines are highlighted in red with a virus icon.
Malware typically looks much different from the rest of the code base. It has very long lines with many program instructions packed into every line. It is typically difficult to read with it's intent being obtuse and obfuscated. Malware usually has no or very few comments and is poorly formatted.
Good program code may be difficult to fully understand by a non-programmer but should make use of human readable function names, variable names and comments. You should be able to get a basic idea for the general function of the code even without knowing any programming.
Handling Malware Files
BitFire flags potential malware in any PHP or JavaScript file with a virus icon. To see the details of why the file was flagged, click on the "Diff" If you find malware on your system and you have purchased the PRO version of BitFire you can use BitFire's "repair" functionality to download the original file from the official WordPress repository. If the file is not in the official WordPress repository you should remove the infected plugin or theme and re-install the theme or plugin from source.
If the file does not exist in the official WordPress repository, is not custom plugin or theme file and is a just malware, you should be safe to "delete" the file. You can instruct BitFire to do this for you, or you can use your favorite file editor to delete the file yourself.
Handling Benign (good) Files
If BitFire miss-identifies a file as potential malware (this usually happens with programs that use the call_user_func() PHP function. You have several options how you can handle it. If it is a known file (a plugin or theme downloaded from the official WordPress repository) you should repair the file. If you are sure that the code modification is benign, you can also choose to "allow" the file "as-is" and it's signature will be excluded from future scans.